In light of the current situation in Ukraine, the Australian Cyber Security Centre (ACSC) is urging all Australian organisations to adopt an enhanced cyber security position.
Background
Over the past two weeks, an escalation in conflict between Russia and Ukraine has resulted in a significant increase in observed cyber-attacks. From mid-February the Ukrainian Government and banking institutions have been experiencing a series of distributed denial of service (DDoS) attacks. More recently, a new wiper malware variant name HermeticWiper was discovered in Ukraine and a number of Ukrainian Government organisation websites have been defaced.
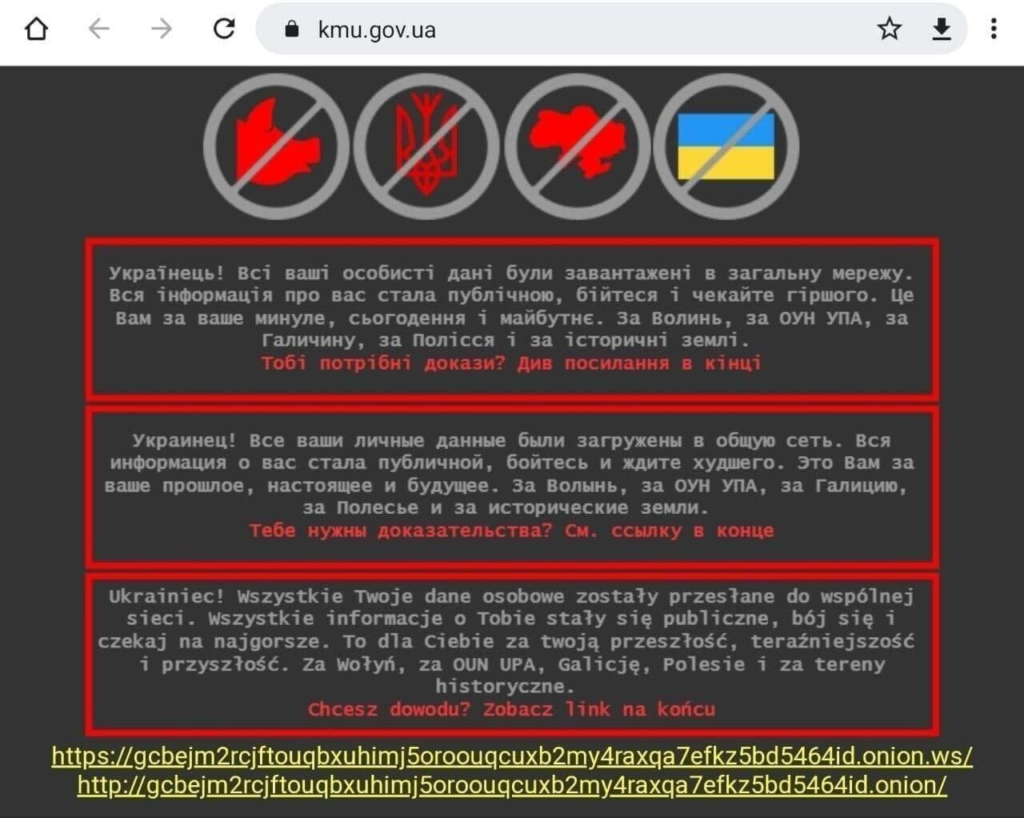
Website defacement message. A new message in red font translates to “Do you need proof, see the link at the end.”
Many Western Governments, including Australia, are now issuing warnings to prepare for cyber-attacks that may disable, disrupt or destroy critical infrastructure. It is expected that future attacks may target Western nations in retaliation for sanctions imposed on Russia.
Whilst the ACSC is not aware of any current or specific threats to Australian organisations, it is expected that businesses may be affected through unintended disruption or uncontained malicious cyber activities. As such, the ACSC is recommending Australian organisations adopt an enhanced security posture and increase monitoring for threats.
What to Expect
The following Tactics, Techniques and Procedures (TTPs) are likely:
- Initial Access – Spear phishing emails may be sent with malicious HTML attachments or links to malicious domains, using URL shortening services to mask the link. Brute force techniques may be used to identify valid M365 or domain credentials, targeting VPN and other Internet-facing services.
- Persistence – Threat actors have been observed maintaining persistent access for at least six months using a variety of downloaded malware, DLLs and PowerShell scripts.
- Privilege Escalation – Cloud Administrator’s privileged accounts have been targeted to generate AAD tokens, create users and grant roles to users and applications.
- Credential Access – Distributed and large-scale targeting using password spray and password guessing has been observed.
- Lateral Movement – As compromised accounts are identified and have their passwords reset, threat actors have pivoted to other accounts to maintain access.
- Collection – M365 resources such as SharePoint pages, user profiles and emails may be accessed using compromised credentials.
How to Stay Secure
The ACSC is recommending that organisations urgently adopt an enhanced cyber security posture through the following:
- Review the Indicators of Compromise (IOC) contained ACSC’s advisory to determine if related activity has occurred on your organisation’s network.
- Ensure that logging and detection systems in your environment are fully updated and functioning and apply additional monitoring of their networks where required.
- Assess your preparedness to respond to any cyber security incidents, and review incident response and business continuity plans.
- Implement the Essential Eight mitigation strategies from the ACSC’s Strategies to Mitigate Cyber Security Incidents as a baseline.
The ACSC is monitoring the situation and is able to provide assistance or advice as required. Organisations that have been impacted or require assistance can contact the ACSC via 1300 CYBER1 (1300 292 371). Read the full ACSC advisory here: https://www.cyber.gov.au/acsc/view-all-content/advisories/2022-02-australian-organisations-should-urgently-adopt-enhanced-cyber-security-posture.
Sources
ACSC – 022-02: Australian organisations should urgently adopt an enhanced cyber security posture
https://www.cyber.gov.au/acsc/view-all-content/advisories/2022-02-australian-organisations-should-urgently-adopt-enhanced-cyber-security-posture



